Jun . 21, 2024 13:52
Back to list
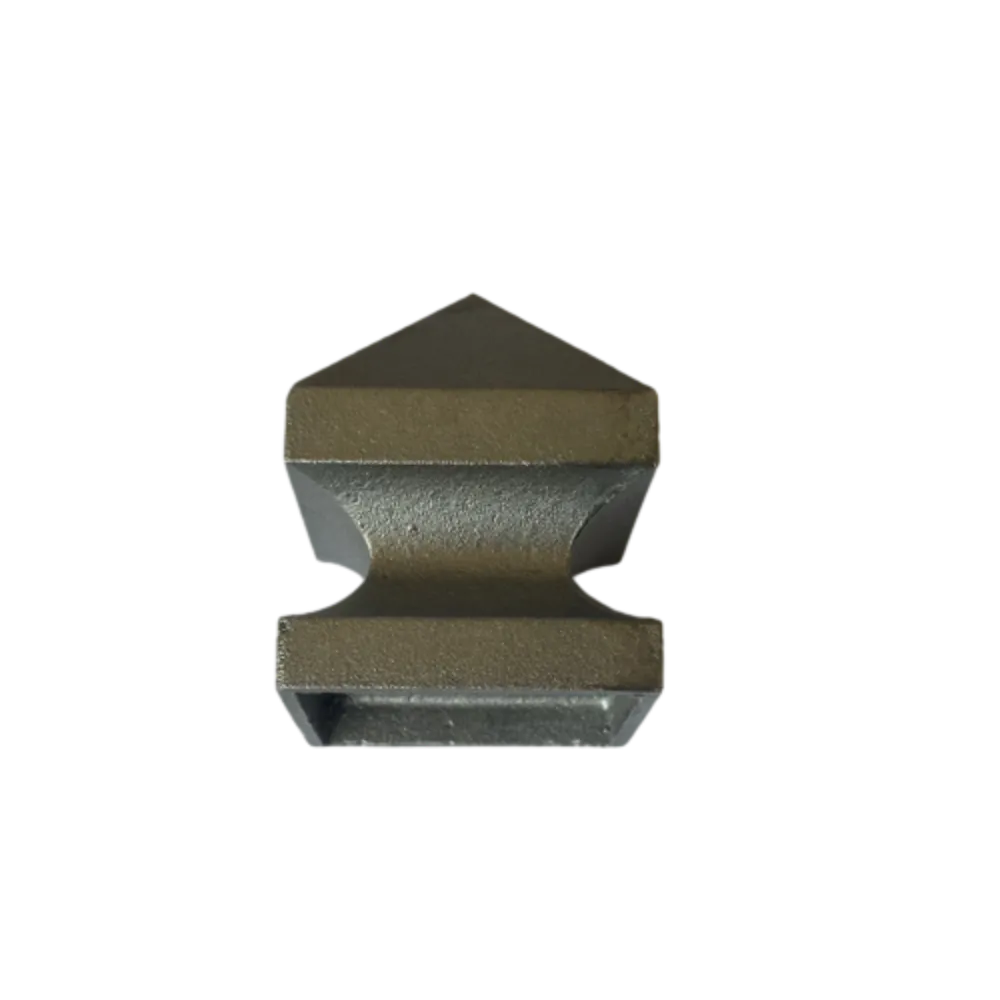
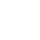
SS gate handle design optimization.
Designing Secure and Efficient Gateways for Network Traffic Management
Abstract
In today's interconnected world, network gateways play a crucial role in managing and controlling traffic flow between different networks. As the number of devices and applications grows exponentially, ensuring the security and efficiency of these gateways has become an increasingly challenging task. This article discusses the essential design considerations for secure and efficient gateways, including the use of advanced encryption techniques, traffic shaping algorithms, and load balancing mechanisms. By following these guidelines, network administrators can create robust gateways that provide reliable access control, protect against cyber threats, and optimize network performance.
Introduction
A network gateway acts as a bridge between two or more networks, enabling communication between devices and systems from different environments. With the proliferation of the Internet of Things (IoT), cloud computing, and mobile devices, the volume and complexity of network traffic have increased significantly. This has placed immense pressure on gateway designers to create solutions that can handle high volumes of data while maintaining optimal performance and security.
Design Considerations
1. Encryption Techniques To ensure the confidentiality and integrity of data transmitted over the network, gateways must employ robust encryption algorithms. Advanced encryption standards (AES) and public key infrastructure (PKI) are two commonly used techniques that provide strong encryption and authentication capabilities. Implementing these technologies helps prevent unauthorized access and data breaches.
2. Traffic Shaping Algorithms Network traffic shaping involves controlling the rate at which data is transmitted to prevent congestion and ensure optimal performance. Various algorithms, such as leaky bucket and token bucket, can be employed to shape traffic and prioritize critical applications. These algorithms help maintain a balance between network utilization and quality of service (QoS).
3
3 3
3
3
3 ss gate handle design. Load Balancing Mechanisms Load balancing distributes incoming network traffic across multiple servers or resources to improve performance, reliability, and scalability. Implementing load balancing techniques, such as round-robin, least connections, and content-based routing, ensures that no single server becomes overwhelmed with traffic. This helps prevent downtime and enhances the overall user experience.
4. Scalability As the number of devices and networks connected to the gateway increases, it becomes essential to design a scalable solution that can accommodate future growth. This may involve using virtualization technology to create multiple instances of the gateway on a single hardware platform or employing load balancing techniques to distribute traffic across multiple gateways.
5. Management and Monitoring Effective management and monitoring of the gateway are critical for maintaining optimal performance and security. Administrators should have real-time visibility into network traffic, system health, and security events. This enables them to quickly identify and resolve issues, as well as detect and respond to potential threats.
Conclusion
Designing secure and efficient gateways requires a comprehensive understanding of the various challenges and considerations involved. By employing advanced encryption techniques, traffic shaping algorithms, load balancing mechanisms, and scalable design principles, network administrators can create robust gateways that provide reliable access control, protect against cyber threats, and optimize network performance. Ongoing management and monitoring are also essential to ensure the ongoing success and effectiveness of these gateways in today's dynamic network environment.
ss gate handle design. Load Balancing Mechanisms Load balancing distributes incoming network traffic across multiple servers or resources to improve performance, reliability, and scalability. Implementing load balancing techniques, such as round-robin, least connections, and content-based routing, ensures that no single server becomes overwhelmed with traffic. This helps prevent downtime and enhances the overall user experience.
4. Scalability As the number of devices and networks connected to the gateway increases, it becomes essential to design a scalable solution that can accommodate future growth. This may involve using virtualization technology to create multiple instances of the gateway on a single hardware platform or employing load balancing techniques to distribute traffic across multiple gateways.
5. Management and Monitoring Effective management and monitoring of the gateway are critical for maintaining optimal performance and security. Administrators should have real-time visibility into network traffic, system health, and security events. This enables them to quickly identify and resolve issues, as well as detect and respond to potential threats.
Conclusion
Designing secure and efficient gateways requires a comprehensive understanding of the various challenges and considerations involved. By employing advanced encryption techniques, traffic shaping algorithms, load balancing mechanisms, and scalable design principles, network administrators can create robust gateways that provide reliable access control, protect against cyber threats, and optimize network performance. Ongoing management and monitoring are also essential to ensure the ongoing success and effectiveness of these gateways in today's dynamic network environment.
 3
3
3
3 ss gate handle design. Load Balancing Mechanisms Load balancing distributes incoming network traffic across multiple servers or resources to improve performance, reliability, and scalability. Implementing load balancing techniques, such as round-robin, least connections, and content-based routing, ensures that no single server becomes overwhelmed with traffic. This helps prevent downtime and enhances the overall user experience.
4. Scalability As the number of devices and networks connected to the gateway increases, it becomes essential to design a scalable solution that can accommodate future growth. This may involve using virtualization technology to create multiple instances of the gateway on a single hardware platform or employing load balancing techniques to distribute traffic across multiple gateways.
5. Management and Monitoring Effective management and monitoring of the gateway are critical for maintaining optimal performance and security. Administrators should have real-time visibility into network traffic, system health, and security events. This enables them to quickly identify and resolve issues, as well as detect and respond to potential threats.
Conclusion
Designing secure and efficient gateways requires a comprehensive understanding of the various challenges and considerations involved. By employing advanced encryption techniques, traffic shaping algorithms, load balancing mechanisms, and scalable design principles, network administrators can create robust gateways that provide reliable access control, protect against cyber threats, and optimize network performance. Ongoing management and monitoring are also essential to ensure the ongoing success and effectiveness of these gateways in today's dynamic network environment.
ss gate handle design. Load Balancing Mechanisms Load balancing distributes incoming network traffic across multiple servers or resources to improve performance, reliability, and scalability. Implementing load balancing techniques, such as round-robin, least connections, and content-based routing, ensures that no single server becomes overwhelmed with traffic. This helps prevent downtime and enhances the overall user experience.
4. Scalability As the number of devices and networks connected to the gateway increases, it becomes essential to design a scalable solution that can accommodate future growth. This may involve using virtualization technology to create multiple instances of the gateway on a single hardware platform or employing load balancing techniques to distribute traffic across multiple gateways.
5. Management and Monitoring Effective management and monitoring of the gateway are critical for maintaining optimal performance and security. Administrators should have real-time visibility into network traffic, system health, and security events. This enables them to quickly identify and resolve issues, as well as detect and respond to potential threats.
Conclusion
Designing secure and efficient gateways requires a comprehensive understanding of the various challenges and considerations involved. By employing advanced encryption techniques, traffic shaping algorithms, load balancing mechanisms, and scalable design principles, network administrators can create robust gateways that provide reliable access control, protect against cyber threats, and optimize network performance. Ongoing management and monitoring are also essential to ensure the ongoing success and effectiveness of these gateways in today's dynamic network environment. Latest news
-
Wrought Iron Components: Timeless Elegance and Structural StrengthNewsJul.28,2025
-
Window Hardware Essentials: Rollers, Handles, and Locking SolutionsNewsJul.28,2025
-
Small Agricultural Processing Machines: Corn Threshers, Cassava Chippers, Grain Peelers & Chaff CuttersNewsJul.28,2025
-
Sliding Rollers: Smooth, Silent, and Built to LastNewsJul.28,2025
-
Cast Iron Stoves: Timeless Heating with Modern EfficiencyNewsJul.28,2025
-
Cast Iron Pipe and Fitting: Durable, Fire-Resistant Solutions for Plumbing and DrainageNewsJul.28,2025
-
 Wrought Iron Components: Timeless Elegance and Structural StrengthJul-28-2025Wrought Iron Components: Timeless Elegance and Structural Strength
Wrought Iron Components: Timeless Elegance and Structural StrengthJul-28-2025Wrought Iron Components: Timeless Elegance and Structural Strength -
 Window Hardware Essentials: Rollers, Handles, and Locking SolutionsJul-28-2025Window Hardware Essentials: Rollers, Handles, and Locking Solutions
Window Hardware Essentials: Rollers, Handles, and Locking SolutionsJul-28-2025Window Hardware Essentials: Rollers, Handles, and Locking Solutions -
 Small Agricultural Processing Machines: Corn Threshers, Cassava Chippers, Grain Peelers & Chaff CuttersJul-28-2025Small Agricultural Processing Machines: Corn Threshers, Cassava Chippers, Grain Peelers & Chaff Cutters
Small Agricultural Processing Machines: Corn Threshers, Cassava Chippers, Grain Peelers & Chaff CuttersJul-28-2025Small Agricultural Processing Machines: Corn Threshers, Cassava Chippers, Grain Peelers & Chaff Cutters